The SIP proxy usually accepts a registration from all SIP users who register themselves with a valid domain and are known to the system as a SIP user. If under in the section SIP users you enable the option Force local authentication, the only subscribers who can register at the SIP proxy are those stored in a user table with the appropriate access data.
The button SIP users opens the dialog for configuring the authentication data of the SIP users (terminal equipment, remote stations or software clients) that do not use the default parameters of an upstream SIP PBX line.
Depending on the model you can create different numbers of SIP users, whereby identical names or identical numbers are not permitted.
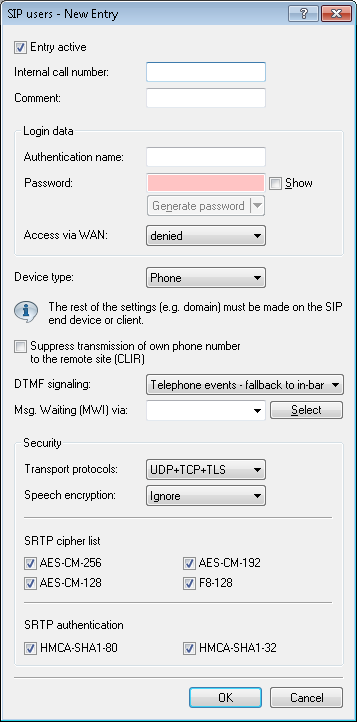
- Entry active
- Activates or deactivates this entry.
- Internal telephone number
-
- Telephone number of the SIP phone
- Name of the user (SIP URI)
- Switchboard number of the SIP PBX, followed by a #. Your SIP PBX must be in the same network as your device, either locally or connected via VPN (internal SIP trunk connection).
- Comment
- Comment about this SIP user.
- Authentication name
- Name for authentication at the SIP proxy, and also to any upstream SIP PBX when the user's domain is the same as the domain of a SIP PBX line. This name is required if registration is mandatory (e.g. when logging in to an upstream SIP PBX or when Force local authentication is set for local users).
- Password
- Password for authentication to the SIP proxy, and also to any upstream SIP PBX, when the user's domain is the same as the domain of a SIP PBX line. It is possible for users to log in to the local SIP proxy without authentication (Force local authentication is deactivated for SIP users) and where applicable to an upstream SIP PBX using a shared password (Standard password on the SIP PBX line).
- Access from WAN
- Permission for SIP users to authenticate via a WAN connection. Possible values are:
- Denied (default)
- Only via VPN
- Device type
- Specify what type of device is used by the SIP user.
- Hide your telephone number from the person being called
- Switches the transmission of the calling-line identifier on/off.
- DTMF signaling
- Depending on the requirements, it may not be sufficient to transmit "inband" DTMF tones if a SIP receiver cannot recognize these. In this case, it is possible to configure an alternative method of DTMF transmission for All-IP connections.
- Only in-band (in audio)
- The tones are transmitted as DTMF tones (G.711) in the RTP (voice) stream.
- Only SIP info
- The DTMF tones are transmitted "out-of-band" as a SIP-info message with the parameters Signal and Duration (as per RFC 2976). There is no parallel transmission of G.711 tones.
- Telephone events - fallback to in-band (default)
- The DTMF tones are transmitted as specially marked events within the RTP stream (as per RFC 4733). There is no parallel transmission of G.711 tones. If the call-initialization SDP message does not include telephone-event signaling, negotiations fallback to inband transfer as per G.711.
- Telephone events - fallback to SIP info
- The DTMF tones are transmitted as specially marked events within the RTP stream (as per RFC 4733). There is no parallel transmission of G.711 tones. If the call-initialization SDP message does not include telephone-event signaling, negotiations fallback to transfer as per SIP-Info message.
- Msg. Waiting (MWI) via
-
The presence of voice messages left on your provider's online mailbox are signaled by notifications on the device. Signaling occurs in different ways depending on the terminal type. Select the line for which this function should be enabled from the list of configured SIP lines under . Note: Notification only occurs if the provider supports this function.
- Transport protocols
- Select a protocol used by this user to communicate with the local SIP server. If the appropriate protocol is not selected, SIP requests from this user will be rejected with a SIP error response (SIP/406). This ensures that no users are able to register with a protocol that has not been allowed here.
- UDP
- All SIP packets to this SIP user are transmitted via connectionless UDP. Most SIP users support this setting.
- TCP
- All SIP packets to this SIP user are transmitted via connection-oriented TCP. The TCP connection is maintained for the duration of the registration.
- TLS
- All SIP packets to this SIP user are transmitted connection-oriented. Also, all SIP packets are encrypted.
- Speech encryption
- Use this entry to specify the protocol used to transmit the voice data (RTP/SRTP) of a call to the local SIP server.
- Reject
- There is no encryption proposal for calls by this user. Calls by this user with an encryption proposal are rejected. The voice channel is never encrypted.
- Ignore
- There is no encryption proposal for calls by this user. However, calls from this user with an encryption proposal are accepted. However, the voice channel is never encrypted.
- Prefer
- Calls by this user cause an encryption proposal. Calls from this user without an encryption proposal are also accepted. The voice channel is only encrypted if the user supports encryption.
- Force
- Calls by this user cause an encryption proposal. Calls by this user without a corresponding encryption proposal are ignored. The speech channel is either encrypted or is not established.
Important: If you require the encrypted transmission of voice data, the signaling must also use an encrypted channel. Otherwise an attack on the unsecured signaling could potentially expose the key for the voice data. Please be aware that your provider may decrypt your voice data and re-transmit it newly encrypted or even unencrypted. The use of SRTP is no guarantee of end-to-end encryption. - SRTP cipher list
- Here you specify the encryption method used for communication with the user. Select one or more of the following methods:
- AES-CM-256
- Encryption is performed using AES256. The key length is 256 bits.
- AES-CM-128
- Encryption is performed using AES128. The key length is 128 bits.
- AES-CM-192
- Encryption is performed using AES192. The key length is 192 bits.
- F8-128
- Encryption is performed using F8-128. The key length is 128 bits.
- SRTP authentication
- With this setting you restrict the amount of (proposed or accepted) SRTP suites that are negotiated with the corresponding user. If you do not select one or more of the ciphers shown below for encrypting the SRTP packets, the device will never propose the corresponding SRTP suite(s) and they are never selected. In this way you can force the best possible encryption.
- HMAC-SHA1-80
- SIP-user authentication is performed with the hash algorithm HMAC-SHA1-80. The hash length is 80 bits.
- HMAC-SHA1-32
- SIP-user authentication is performed with the hash algorithm HMAC-SHA1-32. The hash length is 32 bits.
