To configure the Wireless Intrusion Detection System (WIDS) open LANconfig and go to .
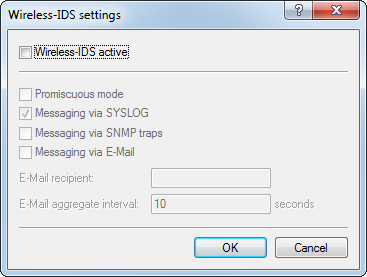
- Wireless-IDS active
- Activates or deactivates the Wireless Intrusion Detection System.
- Promiscuous mode
- With the ("promiscuous mode") enabled, the AP additionally receives packets that were not directed at it, but to other network participants. This mode is necessary to be able to detect the attacks listed below. However, the promiscuous mode affects the performance. For this reason, activating the promiscuous mode automatically causes frame aggregation to be switched off.
- Messaging via SYSLOG
- Activates or deactivates the messaging via SYSLOG. The generated SYSLOG message has the severity level "INFO" and contains the timestamp, the interface, and the trigger (type of attack and passed threshold).
- Messaging via SNMP traps
- Activates or deactivates the WIDS messaging via SNMP traps.
- Messaging via e-mail
- Activates or deactivates the messaging via e-mail.
Important: An SMTP account has to be configured in order to use messaging via e-mail.
- E-mail recipient
- The e-mail address of the recipient when messaging via e-mail is activated. The field must contain a valid e-mail address.
- E-mail aggregate interval
- This setting sets the delay in seconds before a new e-mail is sent if the WIDS is triggered again. This prevents flooding by e-mail in case of extensive attacks.
Signatures
To configure the various thresholds and measuring intervals (packets per second) of the different WIDS alarm functions, change to . These settings are used by the WIDS to determine if an attack is taking place.
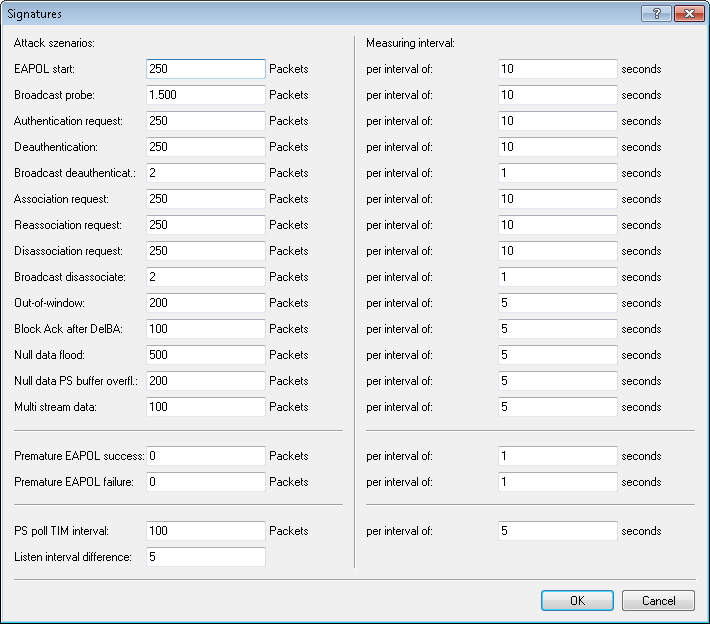
The following attack scenarios can be detected by configuring the thresholds and measuring intervals:
- EAPOL-Start
- Broadcast probe
- Authentication request
- Deauthentication request (*)
- Broadcast deauthentication
- Association request
- Reassociation request
- Disassociation request (*)
- Broadcast disassociate
- Out-of-window
- Block Ack after DelBA
- Null data flood
- Null data PS buffer overflow
- Multi stream data
- Premature EAPOL success (*)
- Premature EAPOL failure (*)
- PS poll TIM interval
- Listen interval difference
There are typical default values set for the different attack scenarios.
Important: (*) These attacks are only detected if promiscuous mode is
active.
