The following tutorial will configure an EAP client against an EAP server.
- Create two certificates or certificate containers, for example with the LANCOM SCEP CA or OpenSSL.
-
Import a certificate into the VPN gateway and a certificate into the RADIUS server.
Important: Make sure the Subject Alternative Name (SAN) matches the valid DNS name of the VPN gateway and that the VPN client contacts the gateway under this DNS name.
- Establish the trust relationship by importing the valid CA certificate into the IKEv2 EAP client.
-
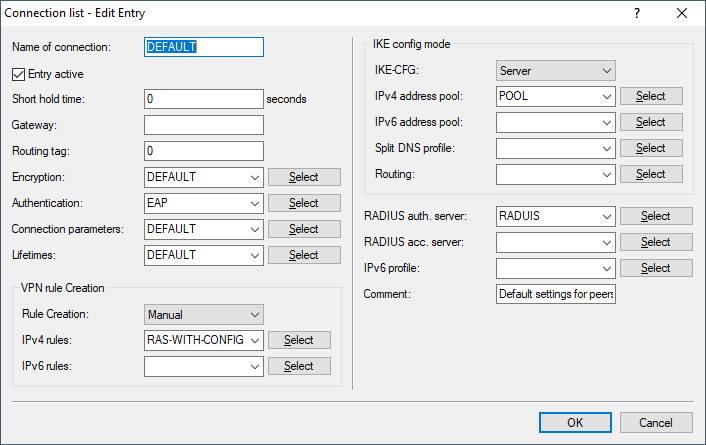
Modify the DEFAULT entry of the IKEv2 remotes table under VPN > IKEv2/IPSec > VPN connections > Connection list as follows:
-
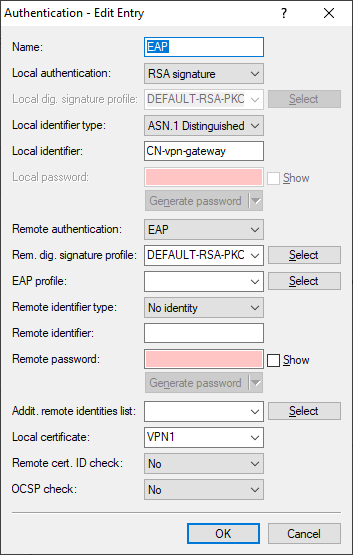
Insert a new row in the IKEv2 Authentication table under VPN > IKEv2/IPSec > Authentication. Local authentication of the VPN gateway uses a certificate (RSA signature), and remote authentication of the clients is done by EAP.
-
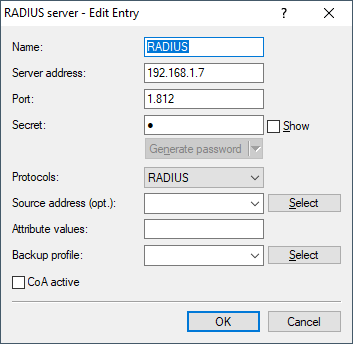
Configure the RADIUS server under VPN > IKEv2/IPSec > Extended settings > RADIUS authentication > RADIUS server.
-
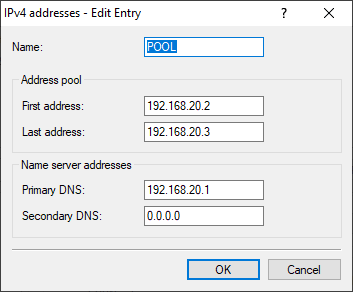
Configure an address pool under VPN > IKEv2/IPSec > IPv4 addresses.