A fascinating look into the engine room of security from the LANCOM Management Cloud
Inconspicuous and undemanding on the inside, tough and relentless on the outside: The nice thing about the security concept of the LANCOM Management Cloud is: Even if you do nothing, the most important thing has already been done to protect your IT infrastructure against damage.
Well, doing nothing is not entirely correct, because the LANCOM cloud-managed security concept does require the permissions to go active on the relevant network, and just a few clicks is all it takes.
Is your company NIS2-compliant and digitally sovereign?
Take control of your network security and Digital Sovereignty. Security requirements are increasing: starting in 2024, the EU NIS2 directive will apply to more companies than ever before and mandate stricter measures for network and information security. Additionally, Digital Sovereignty is becoming an increasingly urgent issue in Europe. It’s worth checking whether your company needs to take action. We provide informational material and practical tips to help:
Learn more about NIS2 and Digital Sovereignty
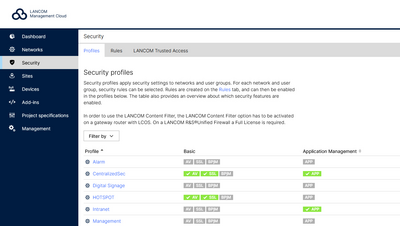
Under the "Security" menu entry, you keep an eye on all security settings in one place. The advantage for you: With just a few clicks, the security profiles become real defensive shields. The story could end here, if only it weren't so exciting to consider the impressive defense machinery that comes to life with this seemingly harmless sequence of clicks. Global rules, such as those for Application Management, Content Filter and Packet Filter, can then be applied to your networks with fine granularity and according to your needs.
The hard way: Controlled admission with special treatment
The basic philosophy of “Unified Threat Management (UTM)”: Viruses, malware, attacks – anything that remotely smells of a threat cannot set foot on company premises, but is rigorously blocked wherever the company IT has contact to the world outside, the Internet.

Bouncer for the IT network
The LANCOM firewalls or the routers with integrated security functions act like unrelenting bouncers – as well as their virtual variants vRouter and vFirewall. You could imagine it were the entrance to the toughest disco in the world: Anyone wanting to get in is frisked, facial recognition and fingerprints are compared to an up-to-date database of criminals with billions of entries and, if there is any doubt, they are taken to a secure room where they are tested for potential aggression. Only then is the decision made: Guest or threat.

Secure Web Gateway
The secure web gateway that is the firewall ignores the header of the data packets, which, like a label on a delivery package, contains information about the sender and recipient and which provides administrative and control data. Nor does it act like a customs officer, who randomly opens suspicious packages and checks their contents. Instead, each individual data packet is thoroughly screened and examined for potential risks.
The technical requirement for this strict door policy is the ability of the firewall to identify itself to the sender as the recipient of the data packets, which it basically is not. All it does is channel the data traffic to the true recipients, i.e. the PCs in the employees' offices.
Modern network management
„Globalization, digitalization and the pandemic have shown companies that the technical prerequisites for a future-proof operation are not yet fully developed. Not only the number, but also the variation of the devices in the network has risen rapidly alone by the fact that a lot of employees have switched to working from home. [...] Today, a network architecture uses a large number of sensors, controllers, routers, switches and access points. In addition, the networking of different locations has become a significant factor in the efficient operation of the entire company due to globalization, internationalization and outsourcing as well as the integration of business areas. What is needed are network management solutions that intelligently organize, optimize and manage these components and enable the network to achieve a holistic security standard.“ – techconsult study from 2022
Total screening: Data packets and X-rays
This masquerade for a good cause involves a security certificate shared by the firewall and the client PCs, so providing the necessary permissions. This is the only way that the firewall can decode the SSL-encrypted data packets, inspect them and, after checking them, encrypt them again and send them on to the client PCs. In the wilds of the Internet, cyber criminals use similar technical configurations and, without the knowledge of the targeted PCs, they launch what are known as "man-in-the-middle attacks".

Deep Packet Inspection
In its more favorable form, this concept implements what we refer to as deep packet inspection: The data is compared with cloud-based, bang up-to-date virus signatures. As a preventative mechanism against as yet unknown virus groups, so-called heuristic analyzes are used to examine the data packets for suspicious patterns and characteristics.

Intrusion Detection / Prevention & Sandboxing
If suspicions remain, the data packets are uploaded to a protective portion of the cloud called a sandbox, where packets can be opened and their behavior examined without fear of damage. Incoming e-mails and their attachments are handled the same way. This rampart uses the best available tools to block and eliminate viruses, malware, Trojans, spam, and phishing attempts.
Also part of the security concept is the intrusion detection and prevention, which combats a wide variety of network attack variants.
Concerted action: Security through an all-round program
This core of LANCOM network security is embedded in a whole series of conditions that are typical to cloud networks and specific to LANCOM solutions, which combine to form a holistic security concept:

VLANs
Dividing the networks into VLANs creates security boundaries and also enables individual security settings according to the requirements of the particular departments or user groups.

Automation
The automatic transmission of network settings to the network components prevents the incorrect settings from manual interventions, which dramatically increases the security – and also the reliability – of the company's IT.

24/7 Monitoring
Meaningful, individually configurable dashboards provide round-the-clock monitoring of the security situation at the company.
Customized security for every case
In terms of prevention, IT managers can still use small manual interventions to customize the protection concept and meet user requirements and restrictions. The aim here is to avoid putting defense-system capabilities to the test in the first place, and to close out possible sources of danger such as vulnerable services and content that are anyway not necessary for professional contexts:
SIEM integration service for cloud-managed LANCOM R&S®Unified Firewalls
Robust security management is essential, especially for larger organizations and managed service providers (MSPs). A centralized Security Information and Event Management (SIEM) system helps organizations detect, analyze, and respond to security threats quickly.
We invite you to enhance your SIEM with our integration service for cloud-managed LANCOM R&S®Unified Firewalls, ensuring comprehensive detection of attacks on your network infrastructure. Further information about technical prerequisites and setup can be found here:

Application Management
This feature allows individual applications or entire groups of applications to be blocked for specific networks with just a few mouse clicks: Do the colleagues in HR really need access to social media? LinkedIn for sure, but Facebook? Maybe not. Peer-to-peer networks can be excluded, be it a file sharer like BitTorrent or Mojo. On the other hand, Facebook may be of vital importance to the marketing department, although they do not need access to Amazon, for example.
Incidentally, blocking services is not the only option here. In the interest of better performance, firewalls can “wave through” some services unchecked: Office 365 presents no risk, and neither do trusted video conferencing systems such as “GoTo”.
Content Filter
Risks are presented not only by services, but by websites too. Merely visiting a page can land you a "drive-by" attack from a Trojan or other malware, without even clicking on anything.
Entire product categories such as pornography, games or drugs are easily blocked with just one click. By the same principle, even entire category groups such as spam or malware can also be shut out. Those who particularly value the protection of minors will also be pleased with the integrated official domain list with content harmful to minors from the "Bundeszentrale für Kinder- und Jugendmedienschutz" (Federal Review Board for Media Harmful to Minors), which is constantly updated.

Multi-layered security architecture like this guarantees the highest level of security – security through control. But: Control isn't everything. There is one more decisive aspect: Trust. And LANCOM stands for that trust. As a subsidiary of the renowned test & measurement specialists Rohde & Schwarz, we have been active in the market for over 20 years. We develop in Germany, assemble in Germany, and host in Germany. Your data in the cloud never crosses the borders of the Federal Republic of Germany and is therefore at all times subject to European and German data protection regulations (GDPR). Highly professional data centers ensure optimal security in terms of data protection and digital sovereignty.
And all of this makes us unique in the cloud-based network management market, and this is how we aim to win your trust.
Everything about network security
There is so much more to know about network security. For example, how to build a secure network at its core, choose the right firewall, and increase network security quickly and efficiently. Or maybe you're interested in which network threats and protection mechanisms exist, which immediate measures secure your existing devices in the shortest possible time, how Unified Threat Management works in detail or how you can eliminate yourself as a possible security risk.
You're welcome to read all about it in our network security theme pages.