What do we mean by network security?
Network security as a term includes all protective measures to safeguard IT infrastructures against unauthorized access, damage, and data loss. These measures can be technical or organizational and ensure a network's confidentiality, integrity, and availability. Encryption technologies and firewalls are just as much a part of professional network security as security and password guidelines and security training.
To comprehensively secure an IT network, multiple layers of protection are needed for every area of the network. It also makes sense to coordinate network and security individually. We show you which security layers are necessary and how extensive your IT security should be, depending on the type of company and the risks of attack.
Current network security and Digital Sovereignty according to NIS2 specifications
Network security is constantly evolving and must address new challenges. The EU NIS2 Directive on network and information security now meets this need by establishing clear specifications and sanctions to enhance cybersecurity in EU companies. A positive side effect is that Digital Sovereignty also strengthens with increased security. Are you affected? If so, what does this mean for your company? Take the NIS2 check and learn more on our topic pages.
More about NIS2 and Digital Sovereignty
Protecting your own IT network
An IT network consists of a large number of individual components: Important data is stored on internal or external servers, employees are equipped with desktop PCs, laptops, and smartphones, a gateway or router provides Internet access and, depending on the size of the company, one or more switches internally network other devices (LAN) such as access points for professional WLAN coverage or even work devices or printers.
In the case of IT networks that are widely distributed and have many branches, protection requires multi-layered and scalable IT security that, in the best case scenario, automatically ensures greater security in the network.
In the following, you will learn which areas are included in network security and what role the type of company and data criticality play in the extent of cybersecurity measures.
Layers and components of professional IT security
Protecting your own IT network involves securing all data, devices, servers, and applications in the network (data security, internal security, and application security), as well as perimeter security, i.e. securing the threshold between the internal and external network – including secure transmission paths and network access (endpoint security, data encryption).
Last but not least, the security of moving data and external cloud applications must not be neglected (security of "data in motion", data protection, and cloud security), nor must the human component (human security awareness).

Internal security
Protection of physical IT equipment, servers, and network access from outside access as well as risk management for disasters / crises through
- Access controls on company premises
- Live monitoring with camera surveillance and activity logs, if required
- Professional next-generation web application UTM firewall
- Regular security patches, functionality checks, and software updates
- Network segmentation

Human security awareness
Protection against human error through
- Extensive IT security and compliance training, in particular on e-mail, password, and social media security, confidentiality regulations, and behavior in the event of an emergency
- Tests such as phishing simulations
- Confidentiality classifications for files and information
- Easily accessible security policies
- Regular reminders and refreshers

Endpoint security
Protection of usage endpoints such as mobile devices, desktops, IoT devices, and sensors, esp. in decentralized and hybrid work environments (BYOD, remote work, external service providers, etc.) through
- Use of VPN clients and ZTNA
- Multi-factor authentication of users
- Clear, centrally managed asset inventory of all devices and virtual resources
- Individual, fine-grained access rights per user
- Regular system updates and security patches
- Clear usage and security guidelines
- Disabling of ports that are not absolutely necessary

Data encryption
Transparent and user-based encryption and decryption in the background through
- VPN or ZTNA networks
- Encryption parameters, algorithms according to current BSI standard
- Regular review of current standards
- Key management concept (PKI) including regular audits

Secure "data in motion"
Protection of the threshold from internal to external network (perimeter) and lateral protection within the own network through
- Multi-layer encryption of data during transmission
- Exclusive use of VPN or ZTNA connections
- Network segmentation through VLANs
- Caching routines to prevent public access
- Regular penetration tests
- User and system specific access keys only to required data

Cloud security
Protection of own cloud applications and careful examination of the security of used external cloud services through
- Clarification of security issues between cloud provider and user
- Physical host access controls
- Secure, GDPR-compliant infrastructure
- Geo-redundancy of the host
- Security patches
- Access controls to corporate data in the cloud
- Absence of backdoors
Minimal protection
Profile: Companies with data worth protecting and moderate availability requirements (e.g. craft businesses)
Typical threats: Phishing (links to malicious websites or downloads with viruses in mails or personal messages) and malware (spyware, ransomware, or browser hijackers via Internet or e-mail)

Protective measures:
- Establish asset inventory (list of hardware such as servers, switches, routers/gateways, access points, PCs, laptops, smartphones, and virtual resources such as drives, clouds, API gateways, and confidential information such as certificates and access), renew, recall or rotate as necessary
- Check and adjust settings and configurations (do not use default settings, configurations, firewall rules, ports or passwords and turn off all unused components and uninstall all non-essential applications)
- Active, regularly updated antivirus program that scans all files that are opened or downloaded
- Active firewall configured by IT specialists
- E-mail security (malware scans, spam filters against spyware, and adware, etc.)
- Password management tools (multi-factor authentication and key management tools for strong, securely created and well-managed passwords)
- Only use cloud applications that have been vetted and approved by the company
Advanced protection
Profile: Companies with more sensitive data and higher availability requirements (e.g. many medium-sized companies / SMEs)
Typical threats: Untargeted attacks like malware / phishing to many mail addresses, spoofing attacks, spamming at typical network vulnerabilities

Protective measures in addition to minimal protection:
- Access control / Network Access Control (NAC) for network and asset access with RFID-based authentication: clear, monitorable and accurate role separation for file, system, and device access, e.g. with the help of LANCOM Trusted Access
- Department or responsibility-based network segmentation, firewalls between networks provide additional lateral protection
- Professional Intrusion Detection System and Intrusion Prevention System (IDS / IPS), e.g. integrated in UTM firewall
- Endpoint security (security software on each device and on management server to protect each network access via devices), e.g. through the Zero-Trust principle
- Data Loss Prevention Software (DLP) to protect critical, confidential data (e.g. preventing email forwarding to external or uploads of company files to open source areas)
- IAAA principle (Identification, authentication, authorization, and audit)
- Cybersecurity strategy for secure, accepted behavior in the internal company network, e.g. with BYOD rules
- Disaster recovery plan in case of natural disasters and cybersecurity contingency plan (e.g. backups, test runs, emergency drills for behavior in case of emergency)
- Ensure digital sovereignty when selecting cloud providers
- Annual vulnerability analysis and penetration tests
High protection
Profile: Companies with highly sensitive data and the highest availability requirements (e.g. large global companies, law firms, tax consultants)
Typical threats: Spear phishing, advanced malware distribution, DDos attacks, targeted hacking attacks

Protection measures in addition to minimal and advanced protection:
- Analysis of activities and threats on the network
- Data protection through file categorization (security labels for confidentiality level with permission-based access and clear processing rights, e.g., open, read, edit, download) and align cloud usage accordingly
- Security Information and Event Management (SIEM) to record and analyze logs and activities
- Threat monitoring (24/7 monitoring of all endpoints)
- PAP concept (packet application packet filter)
- In-house or external security incident response team for detection, root cause analysis, and mitigation
- Personal and corporate vetting for prospective employees, suppliers, and vendors
- Proactive dark web scans for leaked company data in the hands of cybercriminals
- Quarterly vulnerability analysis and penetration tests
- Where applicable, biometric access controls such as retina scans, voice recognition, fingerprint authentication, etc. in particularly sensitive areas
Cyber Security reimagined
„Cyberattacks are omnipresent and constitute a huge threat to the entire economy, regardless of size or industry. The rapid increase in mobile work and cloud services is also making companies even more vulnerable to cyberattacks. While greater flexibility is achieved through remote work and cloud services, the new structures, at the same time, create new attack vectors for cybercriminals which should sound the alarm bells with IT security experts.“ – techconsult study from 2022
That's why the German Federal Office for Information Security (BSI) clearly defines what high-quality network security actually means in plain language, e.g., a clear anti-backdoor policy and the highest European data protection standards. A new milestone in transparency and consumer protection is the BSI's IT Security Label: Manufacturers can test their Internet-enabled products for compliance with the security requirements specified by the BSI. If they assure this, they receive a label via which consumers can access the trusted BSI platform with all relevant security information on the corresponding product via QR code before purchasing the device.
10 questions for Markus Irle, VP Firewall and Security
Markus Irle, Vice President Firewall and Security and Site Manager, answers 10 intriguing questions on network security.
- What is the structure at the heart of a secure network? A secure network is characterized by a clear separation of responsibilities and roles within the individual network components. For example, this requires a separation of the finance, production, and marketing units, including those rules that enforce who is allowed to access which services and resources, when, and under what circumstances, or who can send data to and receive data from the outside world.
- What role does a firewall play? A key one – the firewall is the essential link between the network components and the implementation of security policy. A part of this is checking that data streams comply with policy. The only information and data that any one user can access is that for which the relevant authorization is in place.
- Why are firewalls becoming more widespread? In principle, firewalls reduce the commercial profit from any criminal investment. Cyberattacks are based on a brutal business model that aims to generate maximum income from the least possible effort. The easier it is to attack a target, the greater the reward can be. Unprotected targets are therefore highly attractive to criminals. Firewalls significantly increase the effort and make a target much less viable.
Choosing the right firewall
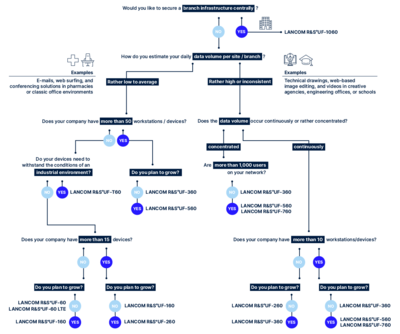
When it comes to protecting corporate data, a professional firewall is an essential part of network security. But depending on the situation, what kind of firewall is best?
In order to protect you to the best possible extent and to maintain a reasonable cost-benefit ratio, a firewall needs to be tailored to various aspects of your network, such as the data traffic, the number of connected devices, or varying data volumes at different times and due to changing numbers of users. All three aspect are decisive for efficient and fast working: The right firewall is always able to process the incoming data volumes – which vary depending on the number of devices – and is also able to deal with peaks in throughput, e.g. during break times at schools or universities. If in doubt it is always advisable to decide in favor of scalability and future viability by choosing the firewall with the higher throughput.
You can try out our Firewall Matchmaker which, designed like a decision tree, guides you step-by-step through various aspects to find the perfect firewall for your company – within minutes:
The good news: Whichever firewall you choose – every LANCOM R&S®Unified Firewall is a next-generation firewall "Engineered in Germany” featuring state-of-the-art Unified Threat Management (UTM) features such as sandboxing, machine learning, and Deep Packet Inspection. Whichever way you decide, your data has the best possible protection – and is guaranteed backdoor-free.
In addition to the LANCOM R&S®Unified Firewalls mentioned here, you can also opt for the virtual LANCOM vFirewall, which offers identical features to the hardware firewalls and, thanks to its flexible license model, “grows” with your demands for UTM performance and network size.
Ask the AI chatbot!
Do you still have questions? Or maybe you cannot find the information you are looking for? The AI-based Digital Assistant will answer all your questions about network security, IT security, and LANCOM R&S®Unified Firewalls – at any time, quickly, and without searching! Alternatively, you can of course still use the contact form.