How do companies and organizations better protect their IT networks?
It seems as inevitable as the proverbial death and taxes: Going hand-in-hand with the rapid increase in digitalization is an exponential growth in the number of attacks on IT systems, and thus on network security. Any security concept must take these dynamic developments into account and continuously adapt to the ongoing threat situation. Effective IT security uses the “onion principle” – attacks are intercepted by successive layers, each of which represents an increasing level of security.
Current network security and Digital Sovereignty according to NIS2 specifications
Network security is constantly evolving and must address new challenges. The EU NIS2 Directive on network and information security now meets this need by establishing clear specifications and sanctions to enhance cybersecurity in EU companies. A positive side effect is that Digital Sovereignty also strengthens with increased security. Are you affected? If so, what does this mean for your company? Take the NIS2 check and learn more on our topic pages.
More about NIS2 and Digital Sovereignty
More IT security
5 important tips for improving network security
IT security aims to protect companies, organizations, and their data from being compromised or threatened. Its essence is to protect IT systems. And of course IT systems in need of protection include IT networks. We recommend five essential protective measures for your IT network to improve IT security and thus also network security:
2nd
Segment your systems. By separating networks, unauthorized access to sensitive company data can be better restricted or limited in time. LANCOM Trusted Access supports you in achieving a particularly fine granular segmentation by user and application according to the zero-trust principle. LANCOM Trusted Access supports you in achieving a particularly fine granular segmentation by user and application according to the zero-trust principle.
Additionally
Secure every single device against cyber attacks in the best possible way! Read here what you should pay attention to regarding your gateways, routers, switches, and access points and how you can increase the security awareness of all employees in your company.
Selecting the right firewall
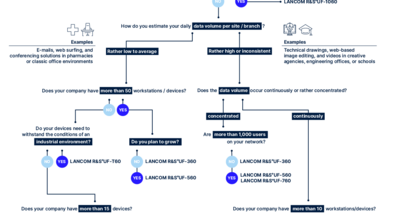
When it comes to cyber protection, individualism is usually a good thing – both when it comes to passwords and choosing the best firewall for your business. The more precisely your firewall is aligned with your data volume, the number of connected devices, or typical traffic patterns, the better it can protect your network. With the Firewall Matchmaker from LANCOM, you can make this alignment in no time at all. With quick answers to just a few questions, you can find the tailor-fit firewall for your purposes immediately, without any lengthy pondering:
SIEM integration service for cloud-managed LANCOM R&S®Unified Firewalls
Robust security management is essential, especially for larger organizations and managed service providers (MSPs). A centralized Security Information and Event Management (SIEM) system helps organizations detect, analyze, and respond to security threats quickly.
We invite you to enhance your SIEM with our integration service for cloud-managed LANCOM R&S®Unified Firewalls, ensuring comprehensive detection of attacks on your network infrastructure. Further information about technical prerequisites and setup can be found here:

Securing devices against cyber attacks
Network security does not necessarily mean expensive new purchases. Your existing devices can also strengthen IT security in the company – and do so immediately!
In true hands-on fashion, you can check the device settings of your routers, gateways, firewalls, switches, and access points and increase their security right as you read this article, without waiting or incurring additional costs.
Take effective immediate action for more network security
Hands-on means practical experience! In addition to tips and hints, case studies are especially helpful in gaining an impression of the actual work with LANCOM R&S®Unified Firewalls.
Optimally protected finances
Financial data is among the most sensitive data for customers and the most coveted by hackers. This makes it all the more important to protect it properly. Otto M. Schröder Bank AG has therefore upgraded its branch's Wi-Fi. With backdoor-free network components, content filter, and high-availability functions, the bank is well protected against network outages and attacks and benefited from a seamless roll-out in the middle of day-to-day business with the help of the LANCOM Management Cloud.

Complete security package for medical practices
Whether attacks on the immune system or on the IT network – thanks to the cooperation of Hasomed, LOOMA and LANCOM, you will never again be at the mercy of this without protection. Find out how the security requirements of therapeutic and medical practices and the IT security guideline of the National Association of Statutory Health Insurance Physicians (KBV) are precisely taken into account and implemented with the highest level of data protection!

Cyber Security reimagined
„Cyberattacks are omnipresent and constitute a huge threat to the entire economy, regardless of size or industry. The rapid increase in mobile work and cloud services is also making companies even more vulnerable to cyberattacks. While greater flexibility is achieved through remote work and cloud services, the new structures, at the same time, create new attack vectors for cybercriminals which should sound the alarm bells with IT security experts.“ – techconsult study from 2022
Ensure network security – defense from malware threats
Secure connection types
We need IT networks wherever data is exchanged digitally. This may involve connections within a company, communication between different company sites, or the connection to a data center or cloud. Secure communication between different branches can be achieved centrally via VPN connections to a head office, or decentral via network security at each site.

Cloud-managed VPN with zero-trust option
VPN stands for Virtual Private Network. A secure connection is established between different parts of the company via a data tunnel. "Zero Trust", on the other hand, describes an even more granular access control with dedicated approvals for individual applications per user. Both concepts are ideal for hybrid working environments with home office, mobile, and external employees.
The LANCOM Trusted Access Client combines both remote access models: As a cloud-managed VPN client, it simplifies the management of VPN access and enables, for example, local user tables or the integration of an Active Directory. With the zero-trust principle activated, micro-segmentation and other features also offer lateral protection against the internal spread of malware.

ZTNA
The “Zero Trust Network Architecture (ZTNA)” is a new and forward-looking concept for secure communication between company departments and employees.
Access rights and the associated protective measures are centrally regulated by a ZTNA broker, which handles the fine-grained distribution of authorizations and security levels on a per-employee and per-service basis. In its final development stage, a ZTNA infrastructure makes traditional VPN clients unnecessary. The LANCOM Trusted Access Client offers a particularly secure and digitally sovereign way to establish the Zero-Trust principle in your own company.
No more beating around the bush! You're here to get serious about network security. So are we. That's why we have equipped a whole range of our routers with the IT Security Label of the German Federal Office for Information Security (BSI). By scanning a QR code, LANCOM customers can see exactly to what extent the respective products comply with the security requirements specified by the BSI and view all relevant IT security information – for conscious, clear, and informed purchasing decisions.
LANCOM Declaration of Trustworthiness
LANCOM Advanced VPN Client
Ask the AI chatbot!
Do you still have questions? Or maybe you cannot find the information you are looking for? The AI-based Digital Assistant will answer all your questions about network security, IT security, and LANCOM R&S®Unified Firewalls – at any time, quickly, and without searching! Alternatively, you can of course still use the contact form.